Vpn Tunnel With Dynamic Ip
The interesting traffic must be initiated from pc2 for the vpn to come up.
Vpn tunnel with dynamic ip. This acl defines the interesting traffic that needs to go through the vpn tunnel. Life will be harder for anyone who tries to hack you. When creating a site to site vpn connection we would use public static ip addresses to connect to each end.
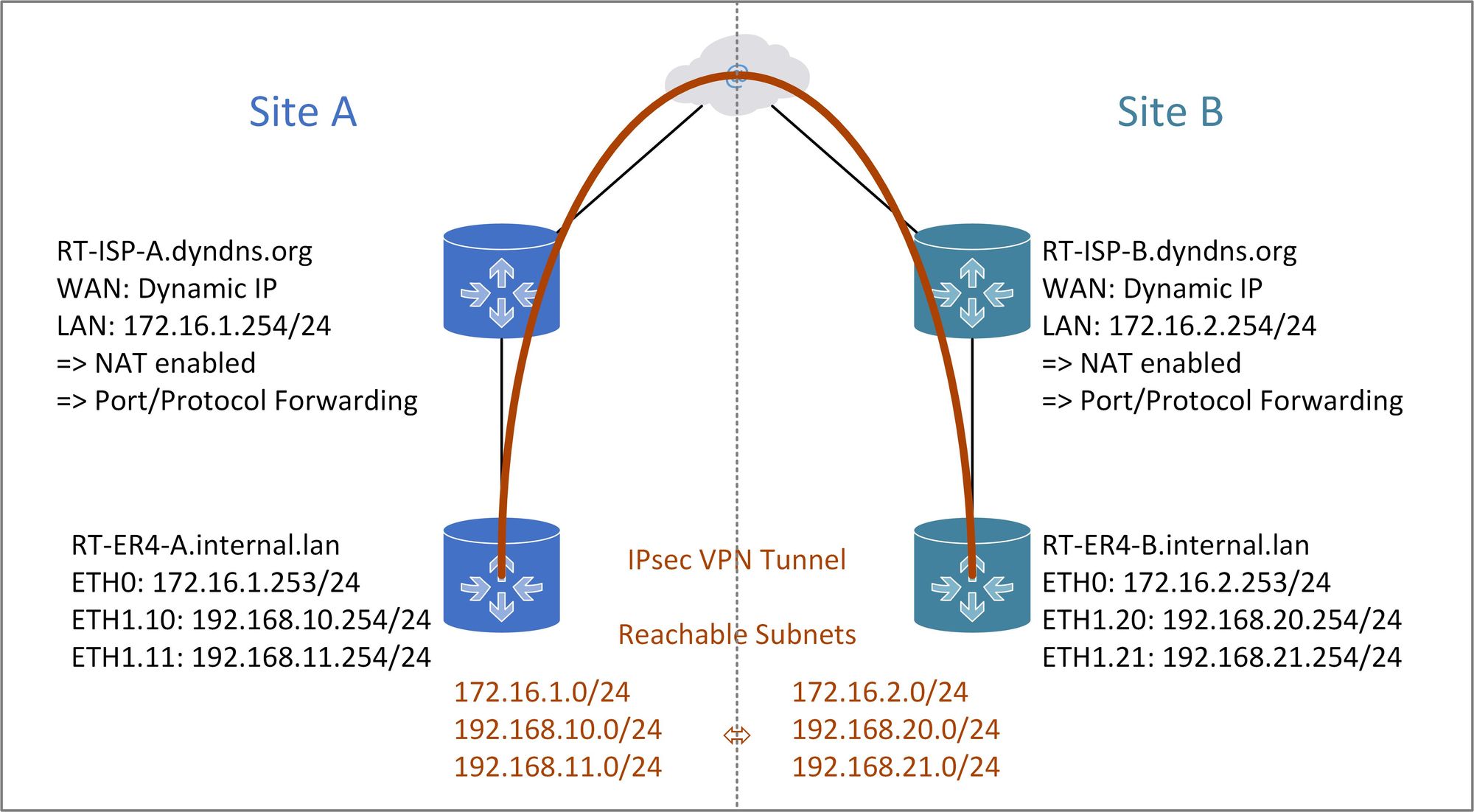
These same directions can be followed when only one side has a dynamic ip address and the other side has a static ip address just use the router s static ip address whenever the dynamic dns name is requested. Hence do not select enable passive mode. Be anonymous and take advantage of fresh starts with dynamic ip vpn.
This acl will be used in step 4 in crypto map. With unlimited and reliable ip addresses from our worldwide servers your device will be automatically updated with its new ip address every time you log in. Treat yourself with a risk free trial vpn.
My wlan is dynamic ip virtual reassembly ip tcp adjust mss 1400 tunnel source dialer0 tunnel destination 75 67 43 79 tunnel mode ipsec ipv4 tunnel protection ipsec profile cryptoprofile. For years we have had a virtual printer on our xenapp servers and worked. It could be anything as long as it is same on the other end.
After verifying that both cradlepoint routers are online that the dynamic dns host s are resolving properly and after verifying that both routers have been configured on different local subnets the directions below will help configure a vpn tunnel between the two routers. We are offering you the fastest dynamic vpn on the market. If one of the ip addresses is not known because it is dynamic such as one obtained via dhcp then an alternative is to use a dynamic crypto map.
The other half of your problem is easy to solve using a dynamic dns service. The dynamic router is configured almost the same way as you normally configure in cases where the router is a dynamic site for ikev2 l2l tunnel with the addition of one command as shown here. The modem notifies the dns service anytime the ip address changes allowing the device at the other end of the tunnel to always be able to connect by consistent name since the ip can change frequently.