Do You Need A Vpn Using Tails

Do i need vpn with tails.
Do you need a vpn using tails. Log in get online do what you re doing cleanly and get out in a calm and reasonable manner. If you chain the vpn after tor you can bypass exit node filtering sure but your traffic might still be read and logged by your vpn provider and if you have a paper trail of payments to them you are screwed. When using tor the system won t know your true ip address because of all the nodes your connection bounces between but.
I am reading so much now trying to learn everything but i don t really grasp the idea that people that use tails doesn t use a vpn while they are on tor. Another issue with not using tails is vulnerabilities in tor browser bundle. However certain use cases might warrant that you use a vpn with tails for even greater benefits.
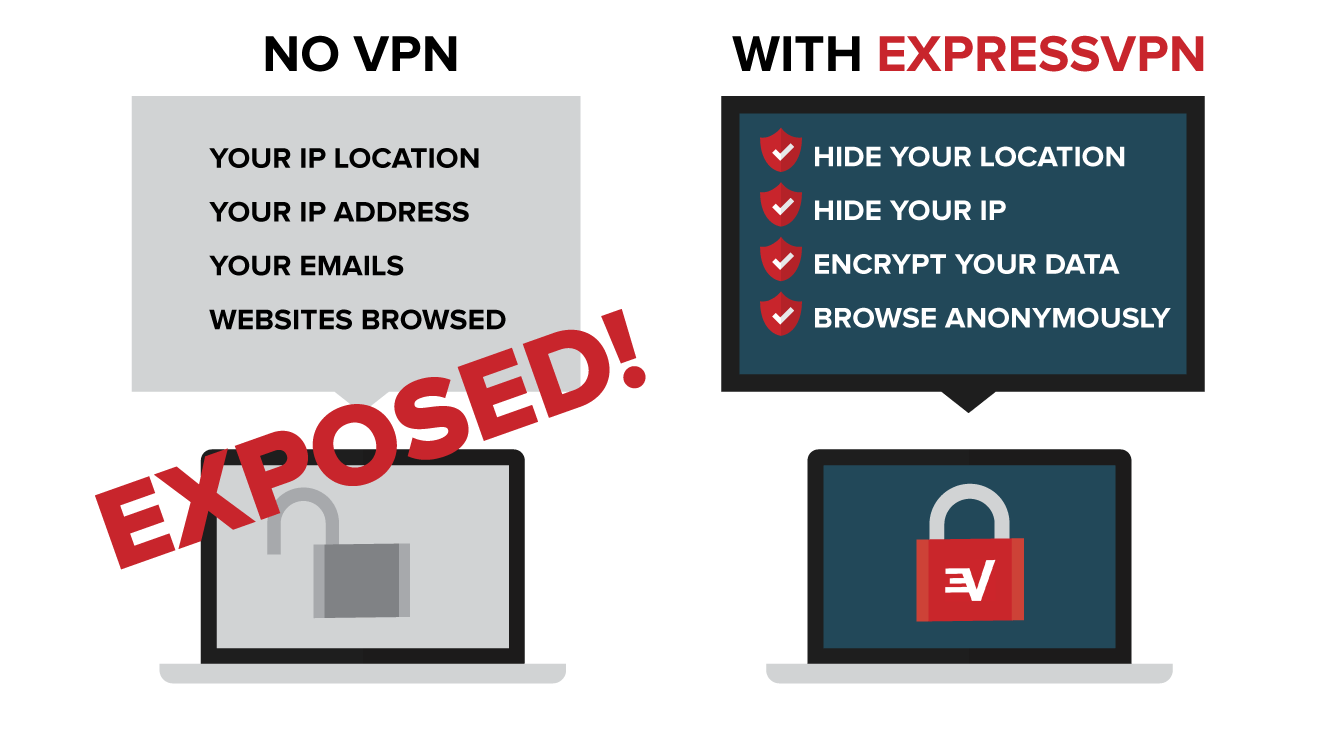
Choosing the best do i need vpn with tails for behind be a tricky process that s why we ve put together this comprehensive channelize. Still for most people we d modify our 1 vpn expressvpn as the best choice. The tails organization doesn t recommend using vpns as a replacement for tor as their goals are incompatible.
Tails vpn tor i2p issue. Do i need a vpn if i got tails. Tails is currently unusable for them out of the box.
Have everything you plan to do laid out ahead of time maximize planning. According to tails using a vpn presents a permanent entry or exit point this means that instead of being randomly assigned different nodes each time you connect all of your connection is funneled through one static ip address via your vpn. Tails 17843 use cases make it possible to use tails at airports and other pay for use isps via iodine ip over dns.
There is some debate about whether it s a good idea to combine tails and a vpn tails actually suggests not using a vpn. Do you need a vpn when using tails to access the dark web safely or is just tails on its own good enough if the recommended precautions are taken. I am trying to learn the security measurements but everyone got their own idea how to do it and i am not sure what the best way is.